Cybersecurity incidents don’t always start with our clients, but they can certainly end there—if the right protections are in place. Today, we’re sharing a real-world example of how a supplier’s compromised account could have led to a breach, and how our security-first approach protected our client.
A Familiar Name, A Dangerous Trap
Earlier today, an employee at one of our client organizations received an email from a trusted supplier. It contained a OneDrive link to a file labeled “NEW PROJECT PROPOSAL.” That alone wouldn’t raise any red flags—after all, collaborating on shared documents is a normal part of business.
What our client’s employee didn’t realize was that the supplier’s Microsoft 365 account had been compromised. A threat actor had gained access, uploaded a malicious PDF to the supplier’s OneDrive, and shared the file with everyone in the supplier’s contact list—including our client.
A Convincing—but Malicious—Chain of Events
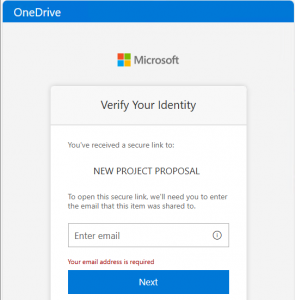 Clicking the link took our client’s employee to a legitimate Microsoft OneDrive verification page, asking him to confirm his email address to access the file. This wasn’t an obvious phishing attempt with strange misspellings or an unfamiliar sender—it was a real OneDrive prompt, because the file truly existed in the supplier’s compromised account.
Clicking the link took our client’s employee to a legitimate Microsoft OneDrive verification page, asking him to confirm his email address to access the file. This wasn’t an obvious phishing attempt with strange misspellings or an unfamiliar sender—it was a real OneDrive prompt, because the file truly existed in the supplier’s compromised account.
Trusting the source, the employee downloaded and opened the PDF. Inside was an embedded link that, when clicked, redirected him to what appeared to be a Microsoft 365 login page. This wasn’t actually a Microsoft page. It was a credential-harvesting site designed to steal login information.
The Moment of Compromise—And The Block That Saved Our Client
The employee, believing he was logging into Microsoft 365, entered his credentials. At this point, the threat actor had everything they needed to attempt access to our client’s Microsoft environment.
But here’s where our security strategy made all the difference.
The attacker’s system immediately tried to log in using the stolen credentials. However, because we had configured Microsoft 365 using security best practices—including Multi-Factor Authentication (MFA), conditional access policies, and login anomaly detection—the attack was stopped in its tracks. The unauthorized attempt was flagged, blocked, and reported before any damage could be done.
Lessons Learned: Security Fatigue and the Importance of Strong Defenses
This event highlights a common challenge: security fatigue. Employees are bombarded with security warnings and login prompts daily. Over time, even the most cautious individuals may lower their guard, especially when dealing with what appears to be a routine business request from a known contact.
The difference between our client and the supplier that got compromised? A well-implemented security framework.
- The supplier’s Microsoft 365 account was vulnerable—likely due to weak security settings, lack of MFA, or a previous credential compromise.
- Our client, on the other hand, had the right protections in place. Even when human error occurred, our layered security measures ensured that the breach attempt failed.
Cybersecurity Is More Than Just Awareness—It’s About Resilience
Education and awareness are critical, but they’re not enough on their own. Businesses must adopt security-first IT strategies that assume mistakes will happen and mitigate the risks accordingly.
That’s where we come in. At Clocktower Technology Services, we specialize in protecting businesses from these very threats. From configuring Microsoft 365 security to providing ongoing cybersecurity training and response, we make sure that when an attack happens—and it will—your business stays protected.
If your organization isn’t confident in its security posture, now is the time to act. Let’s talk about how we can help secure your Microsoft 365 environment and safeguard your business against evolving threats.
Because every organization deserves great security.



